31 January 2025
How to Choose the Best Mobile App Development Company for Your Business Read More - Premium App & Web Development With Limited-Time Savings  Enjoy 20% Off All App & Web Services
Enjoy 20% Off All App & Web Services  Claim Your Offer Today -
Claim Your Offer Today -
In today’s digital world building a secure app in Australia is no longer optional—it’s a business critical.
The country’s cyber threat landscape is intensifying, each year there are thousands of cyber breaches to businesses. While most of these breaches affect smaller businesses, occasionally there are “major” cyber breaches that impact large organisations and a huge number of people.
In the fiscal year 2023-24, the Australian Signals Directorate (ASD) addressed more than 1,100 cyber incidents, with 11% of these attacks targeting critical infrastructure.
Additionally, there was a 12% rise in calls to the Australian Cyber Security Hotline, resulting in over 36,700 inquiries concerning cyber threats.
This continuous surge places businesses of all sizes at considerable risk: not only financial losses but also significant reputational harm and the possibility of facing regulatory penalties.
This guide is specifically designed for CTOs, business owners, and entrepreneurs who are looking to develop a secure mobile application in Australia. CTOs will discover in-depth analyses of secure architecture and compliance with regulations, while founders and startup leaders will receive practical advice on success strategies to build mobile apps for startups and how to balance cost, risk, and speed to market.
Whether you are scaling a fintech startup, launching a health-tech platform, or updating enterprise workflows, it is crucial to understand how to create a secure mobile app in Australia to safeguard your users, your reputation, and your financial performance.
This section provides a comprehensive overview of Australia’s current cybersecurity challenges and why they matter to business leaders.
Let me break it down:
Cybercrime is causing significant disruption to the Australian economy. From mid-2022 to mid-2023, the cost of cybercrime for Australian businesses rose by 14%. The average cost of cybercrime for small businesses is now $46,000; $97,200 for medium businesses; and $71,600 for large businesses. These cyber attacks on our businesses, democratic institutions and critical infrastructure is unacceptable.
The repercussions of a single breach on a business can be catastrophic.
This outlines the genuine cyber threats that Australian enterprises encounter:
Average cost per data breach in Australia: $4.9 million
Each hour your application is non-operational equates to lost revenue.
60% of customers discontinue using applications following a security breach.
This outlines the growing government oversight:
Bottom Line: The threat landscape is increasingly perilous and costly, while regulatory enforcement is tightening. This issue transcends IT; it represents a core business risk that demands the attention and investment of the C-suite.
Building secure Australian app guarantees adherence to regulatory standards, fosters user confidence, and safeguards against cyber threats. Given the stringent data protection laws and the increasing number of breaches, implementing strong security measures provides a competitive advantage and results in long-term financial benefits. Investing in app development within Australia leads to solutions that are globally recognised and prepared for the future. Are you interested in knowing the actual cost cost to create an app in Australia?
Then read our exclusive blog on-
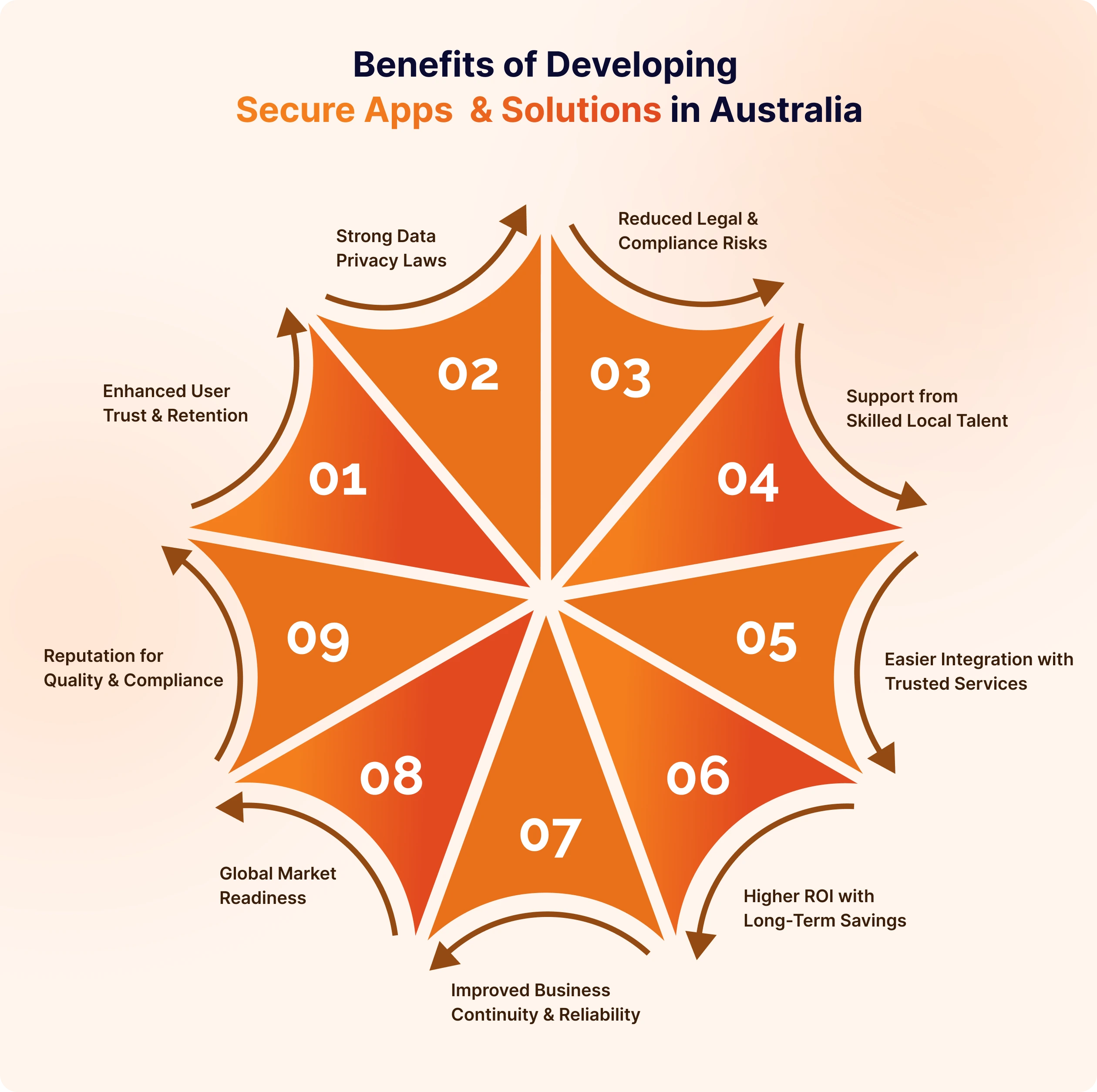
Developing secure applications in Australia guarantees compliance with stringent regulations such as the Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme. Adhering to these requirements reduces legal liabilities, prevents substantial fines (which can reach up to $50 million AUD as said above), and enhances user trust. A compliant application also conforms to GDPR, facilitating global scalability and making it a more secure investment.
Australian consumers place a high value on data security—83% of them abandon applications following breaches. By adopting end-to-end encryption, biometric authentication, and clear data policies, you cultivate customer loyalty. Secure applications receive better ratings, favorable reviews, and enhanced customer retention, thereby reinforcing your brand’s credibility in competitive markets.
Australia experiences a cyberattack every 6 minutes (as reported in 2024). Applications that adhere to OWASP top 10 standards, undergo penetration testing, and utilize real-time threat monitoring can significantly reduce risks. Proactive security measures avert breaches, resulting in cost savings on incident response and damage to reputation.
An app that is security-certified (ISO 27001, SOC 2) sets your business apart on an international scale. Investors and enterprise clients favor apps developed in Australia due to the rigorous regulations in place. Emphasizing security features in your marketing strategy can enhance B2B partnerships and attract more users.
Implementing secure coding practices can decrease post-launch fixes by 40%. By investing in DevSecOps, automated security testing, and cloud-native protections (AWS/GCP), you can ensure that your applications are scalable and future-ready. Reduced costs associated with breaches translate to a higher return on investment over time.
Building a secure app in Australia protects data, guarantees compliance, and fosters trust. By making security a priority, businesses can achieve a competitive edge while safeguarding users and ensuring sustained success in the current digital environment.
Additional Reading: Why Mobile App Security is Important for Your Business? Best Practices Explained.
This section examines the most critical emerging security trends and threats that Australian organizations will encounter in 2026. From AI-driven attacks and defenses to the impending wave of quantum-resistant cryptography, privacy-enhancing technologies, and regulatory changes, we offer a thorough analysis of what lies ahead—and how to prepare.
By comprehending these trends, businesses can make well-informed decisions to develop secure app in Australia, thereby protecting their reputation, customer trust, and operational resilience.
Adaptive security systems are increasingly utilizing AI and machine learning to identify threats before they occur. These technologies are becoming essential for developing secure apps and solutions by facilitating predictive protection against the evolving landscape of cyberattacks in Australia.
How to Implement It in Your App
Incorporate AI-driven security tools (such as Darktrace or Azure Sentinel).
Employ behavioral biometrics (like typing patterns or swipe gestures) for fraud detection.
Utilize anomaly detection APIs to oversee suspicious transactions.
Example:
A banking application that employs AI can flag a transaction as fraudulent if it identifies a user logging in from a new device and promptly transferring substantial amounts.
Quantum computing, although still in its developmental stages, presents a potential threat to existing encryption techniques. Cybercriminals are already employing a “harvest now, decrypt later” strategy—acquiring encrypted information to decipher it later using quantum computing technology.
How to Ensure Your Application is Future-Proof
Implement quantum-resistant algorithms (for instance, NIST-approved CRYSTALS-Kyber).
Transition from RSA to lattice-based cryptographic methods.
Utilize hybrid encryption (which integrates classical and post-quantum algorithms).
Example:
A healthtech application that manages sensitive patient information should begin the process of shifting to post-quantum encryption to mitigate future decryption vulnerabilities.
The principle of “never trust, always verify” is a fundamental trend in application development methodologies. Zero Trust guarantees that all users and devices undergo continuous authentication—this is one of the most effective practices to secure app development in Australia
How to Implement Zero Trust in Mobile Applications
Adopt the “never trust, always verify” principle – Mandate authentication for every action taken.
Employ micro-segmentation to restrict lateral movement in the event of a security breach.
Implement least-privilege access (users are granted only the permissions they absolutely require).
Example:
A corporate application utilising Zero Trust would necessitate multi-factor authentication (MFA) and device verification even for employees accessing internal documents, thereby preventing compromised credentials from providing unrestricted access.
CaaS is revolutionising the manner in which organisations develop secure mobile applications in Australia, particularly for startups and small to medium enterprises (SMEs). Rather than investing in expensive internal security teams, companies can now outsource their security needs to specialised providers who oversee and manage threats around the clock.
How to Enhance Your Application with CaaS
Collaborate with reputable CaaS providers that offer real-time threat monitoring.
Incorporate CaaS APIs during the initial stages of app development.
Ensure adherence to Australian data privacy and security regulations.
Example:
A fintech startup aiming to develop a secure mobile application in Australia can leverage CaaS to safeguard user transactions and minimise operational costs while remaining agile and compliant.
Biometric security techniques—such as facial recognition, fingerprint scanning, and voice identification—are increasingly becoming the norm in secure app development in Australia. They provide a seamless, password-free experience for users while minimising the risk of identity theft or data breaches.
How to Implement Biometrics Effectively
Employ multimodal biometrics for enhanced security layers.
Securely store biometric templates using encryption on the device.
Ensure that fallback methods are equally secure (e.g., two-factor authentication).
Example:
A healthcare application that aims to develop a secure mobile app in Australia can incorporate facial recognition for patient logins—ensuring compliance with HIPAA and facilitating smoother user access.
DevSecOps integrates security into every phase of the development lifecycle. From the design stage to deployment, it assists teams in developing secure apps and solutions in Australia by detecting and addressing vulnerabilities at an early stage.
How to Integrate DevSecOps
Automate security testing within your continuous integration and continuous deployment pipeline.
Educate developers on secure coding methodologies.
Utilise tools such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and dependency scanning from the outset.
Example:
A logistics firm looking to develop a secure mobile app in Australia can leverage DevSecOps to guarantee that new features are inherently secure—thereby reducing risks during fast-paced release cycles.
Additional 2026 Security Considerations
The Australian mobile application market is thriving, yet it faces increasing cyber threats. Given the stringent data protection regulations and the constantly evolving nature of attack strategies, to create a secure mobile app in Australia necessitates a proactive strategy.
To develop a secure application, Australian app developers and businesses must navigate one of the most sophisticated cybersecurity frameworks globally. Adherence to the Privacy Act 1988 and the Australian Privacy Principles (APPs) is essential for any application that processes personal data. These laws impose rigorous requirements on data collection, storage, and sharing, making privacy-by-design an indispensable standard.
This comprehensive guide outlines critical app development practices in Australia to safeguard your users and your business.
Security must be prioritized from the outset—not treated as an afterthought. Adopting a security-first strategy helps to mitigate risks before they escalate into expensive breaches.
Key Actions:
Perform threat modeling during the planning phase to pinpoint risks.
Collaborate with Australian cybersecurity professionals to establish secure architecture.
Educate developers on the OWASP Top 10 vulnerabilities and principles of secure coding.
The Privacy Act 1988 and the Notifiable Data Breaches (NDB) scheme in Australia enforce stringent regulations regarding data management. Failure to comply may result in **penalties reaching $50 million AUD.
Key Actions:
Adhere to the Australian Privacy Principles (APPs) when collecting data.
Ensure all stored and transmitted data is encrypted (using AES-256 and TLS 1.3).
Secure explicit user consent prior to processing personal information.
Weak login credentials represent a significant attack vector. Implementing Multi-Factor Authentication (MFA) and role-based access control (RBAC) can significantly diminish unauthorized access.
Your application’s authentication system should be robust. There are various methods to strengthen the authentication process. Multi-Factor Authentication (MFA) is a widely adopted method to enhance security. Numerous MFA services are available today, including Google Authenticator and SMS-based one-time passwords (OTPs).
On both iOS and Android platforms, you can utilize Face ID and fingerprint scanners. Additionally, enforce minimum password length requirements and a combination of character types. This approach complicates unauthorized access attempts through brute force or guessing.
Key Actions:
Implement MFA (SMS, biometrics, authenticator applications).
Utilize OAuth 2.0 or JWT tokens to ensure secure sessions.
Enforce password policies (minimum of 12 characters, no reuse).
Unencrypted data presents a significant risk for hackers. End-to-end encryption (E2EE) guarantees the safety of data both during transmission and while stored.
Key Actions:
Utilize AES-256 for data at rest.
Implement TLS 1.3 to secure network communications.
Regularly rotate encryption keys.
APIs are key targets for cyberattacks. Unprotected APIs can result in data breaches, DDoS attacks, and violations of compliance regulations.
In the development of mobile applications, it is essential that the communication between the application and external services is secure; this includes APIs or servers. Ensure that all API requests from your application utilize HTTPS instead of HTTP, even when interacting with local or development servers. If sensitive information must be transmitted, confirm that it is encrypted using robust algorithms prior to transmission.
Key Actions:
Employ OAuth 2.0 / JWT for authentication APIs.
Introduce rate limiting to thwart brute-force attacks.
Perform API penetration testing prior to deployment.
Security is not a one-off endeavor—continuous testing identifies vulnerabilities before they can be exploited by hackers.
Regular security assessments are the most effective method to uncover potential weaknesses. By proactively testing your application, you can significantly decrease the chances of a security breach.
We strongly advise conducting manual penetration testing. Automated tools often lack effectiveness. Rather than depending solely on automated testing tools, integrate both manual and automated testing to comprehensively evaluate your application more efficiently.
Key Actions:
Conduct SAST & DAST scans (e.g., Snyk, Burp Suite).
Execute manual penetration tests on an annual basis.
Address critical vulnerabilities without delay.
Even the most robust defense can be compromised. A well-defined incident response plan helps to mitigate damage during a breach.
Key Actions:
Establish breach detection and containment procedures.
Educate staff on emergency response protocols.
Inform affected users within 30 days (NDB compliance).
Building a secure mobile application in Australia is not solely about avoiding penalties—it is also about earning user trust and maintaining a competitive edge. By adhering to these best practices, you ensure compliance, minimise risks, and safeguard the future of your application.
For businesses in need of professional advice, collaborating with developers certified in Australian security standards guarantees compliance and prepares your application for future challenges. Emphasizing security is not merely a matter of regulation; it fosters user confidence in the competitive digital landscape of Australia.
Mobile app development company in Australia such as Dev Story focus on integrating security and compliance at every level of your application, ensuring adherence to Australia’s rigorous regulatory requirements while providing a smooth and reliable user experience. By making security a priority from the outset, you not only safeguard your users and their data but also establish a reputation for dependability in Australia’s fiercely competitive digital arena.
Develop secure apps in Australia with a top certified software development team in accordance to Australian security standards guarantees compliance and prepares your application for future challenges. Emphasising security is not merely a matter of regulation; it fosters user confidence in the competitive digital landscape of Australia.